29 05 2015
Microsoft New Released Exam: 70-341 Dumps Free Download From Braindump2go! (101-110)
We never believe in second chances and Braindump2go brings you the best 70-341 Exam Preparation Materials which will make you pass in the first attempt.We guarantee all questions and answers in our 70-341 Dumps are the latest released, we check all exam dumps questions from time to time according to Microsoft Official Center, in order to guarantee you can read the latest questions!
Vendor: Microsoft
Exam Code: 70-341
Exam Name: Microsoft Core Solutions of Microsoft Exchange Server 2013
Keywords: 70-341 Exam Dumps,70-341 PDF Download,70-341 VCE Download,70-341 Study Guide,70-341 Study Material,70-341 Braindump,70-341 Exam Questions,70-341 Book
QUESTION 101
You have an Exchange Server 2013 organization that contains 20 Mailbox servers.
You plan to create 10 mailbox databases on each Mailbox server.
You need to create a naming convention for all mailbox databases.
What should you include in your naming convention?
A. For each mailbox database, provide a database name that is unique within the organization.
B. For each mailbox database, provide a database name that is unique within the Mailbox server.
C. For each mailbox database file, provide a file name that is unique within the organization.
D. For each mailbox database file, provide a file name that is unique within the Mailbox server.
Answer: A
QUESTION 102
You have an Exchange Server organization that contains three servers that have Exchange Server 2013 installed and one server that has Exchange Server 2010 installed.
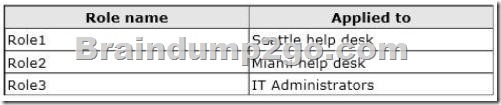
You create the custom RBAC roles shown in the following table.
The Seattle help desk manages all of the users in an organizational unit (OU) named Seattle.
The Miami help desk manages all of the users in an OU named Miami.
The IT Administrators manage all of the users in the forest.
You need to recommend which commands must be run to prevent only the members of both help desks from modifying the properties of users who have a department attribute value of Manager. Which three commands should you run? (Each correct answer presents part of the solution. Choose three.)
A. new-managementscope "executive users exclusive scope"
-recipientrestrictionfilter { department -eq "manager" } -exclusive sorce
B. new-managementroleassignment -name "managers" -securitygroup "managers"
-role "mail recipients" -exclusiverecipientwritescope "executive users exclusive scope"
C. new-roleassignmentpolicy -name "limited end user policy" -roles "mypersonalinformation".
D. new-rolegroup -name "managers" -roles "mail recipients" -members admins
E. new-rolegroup -name "help desk" -roles "mail recipients" -members admins
Answer: ABD
Explanation:
Note:
– (A) Use the New-ManagementScope cmdlet to create a regular or exclusive management scope. After you create a regular or exclusive scope, you need to associate the scope with a management role assignment.
To associate a scope with a role assignment, use the New-ManagementRoleAssignment cmdlet.
– (B) Use the New-ManagementRoleAssignment cmdlet to assign a management role to a management role group, management role assignment policy, user, or universal security group (USG).
QUESTION 103
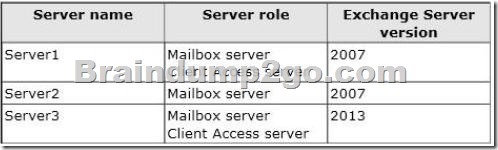
You have an Exchange Server 2007 organization.
You recently deployed a server that has Exchange Server 2013 installed.
The Exchange Server organization contains three servers.
The servers are configured as shown in the following table.
Server2 contains a mailbox for a user named User1.
You move the mailbox of User1 to Server3.
After the move, User1 fails to access his mailbox by using Outlook Web App. Users who have mailboxes on Server1 and Server2 can access their mailboxes by using Outlook Web Access.
You need to ensure that User1 can access his mailbox from the Internet by using Outlook Web App at https://mail.contoso.com.
The solution must ensure that users who have mailboxes on Server1 and Server2 can continue to use Outlook Web Access.
Which three actions should you perform? (Each correct answer presents part of the solution. Choose three.)
A. Export the certificate on Server1 and import the certificate to Server 3.
B. On all of the Exchange servers, install a new certificate that contains the mail.contoso.com
and legacy.contoso.com names.
C. Redirect all of the traffic from the Internet for mail.contoso.com to Server3.
D. On all of the Exchange servers, install a new certificate that contains the
Server1.contoso.com, server2.contoso.com, server3.contoso.com, and
legacy.contoso.com names.
E. Create a host (A) record named legacy.contoso.com that points to Server1.
Answer: ABE
Explanation:
Client Connectivity in an Exchange 2013 Coexistence Environment
http://technet.microsoft.com/en-US/exdeploy2013/Checklist?state=2419-W-FgBEAgAAQACAAIECAQAAAAg~
http://technet.microsoft.com/en-US/exdeploy2013/Checklist?state=2419-W-EQBEAgAAQACAAIECAQAAAAg~
QUESTION 104
You host Exchange Server 2013 organizations for several hundred tenants.
The infrastructure contains several custom transport agents.
You need to prevent the transport agents from overloading the processors on one of the Exchange servers.
Which cmdlet should you run?
A. Set-WorkloadPolicy
B. Set-ResourcePolicy
C. Set-TransportAgent
D. Set-ThrottlingPolicy
Answer: A
QUESTION 105
Drag and Drop Question
You have an Exchange Server 2013 organization that contains a server named EX1.
You have a user named User1 in the marketing department.
You need to prevent User1 from submitting more than 50 email messages per minute to the Exchange Server organization by using Microsoft Outlook.
Which three commands should you run? To answer, move the three appropriate commands from the list of commands to the answer area and arrange them in the correct order.
![105_thumb[1] 105_thumb[1]](http://examgod.com/bdimages/41dd374e231d_E071/105_thumb1_thumb.jpg)
Answer:
![105-1_thumb[2] 105-1_thumb[2]](http://examgod.com/bdimages/41dd374e231d_E071/105-1_thumb2_thumb.jpg)
Explanation:
Note:
Box 1:
– Use the New-ThrottlingPolicy cmdlet to create a non-default user throttling policy.
– The MessageRateLimit parameter specifies the number of messages per minute that can be submitted to transport.
Box 3:
– Use the Set-Mailbox cmdlet to modify the settings of an existing mailbox.
You can use this cmdlet for one mailbox at a time.
/ parameter: ThrottlingPolicy
Microsoft.Exchange.Configuration.Tasks.ThrottlingPolicyIdParameter
QUESTION 106
Drag and Drop Question
You have an Exchange Server 2013 organization that contains four servers named EX1, EX2, EX3, and EX4.
All of the servers are members of a database availability group (DAG) named DAG1.
Each server has a copy of a mailbox database named DB1.
DB1 has the following characteristics:
– The replay lag time on Ex4 is set to 14 days.
– Single item recovery on all of the servers is set to 14 days.
– None of the servers have Volume Shadow Copy Service (VSS) backups.
Ex4 has a folder named F:\RDB that is used to store database files during restore operations. Twenty days ago, a user named User1 deleted an email message that had a subject of "Sales Report".
You need to restore the deleted email message to the mailbox of User1.
You copy the lagged database and the log files that are older than 20 days to F:\RDB.
Which three actions should you perform? To answer, move the three appropriate actions from the list of actions to the answer area and arrange them in the correct order.
![106_thumb[1] 106_thumb[1]](http://examgod.com/bdimages/41dd374e231d_E071/106_thumb1_thumb.jpg)
Answer:
![106-1_thumb[1] 106-1_thumb[1]](http://examgod.com/bdimages/41dd374e231d_E071/106-1_thumb1_thumb.jpg)
QUESTION 107
Your company has three offices. Each office is configured as an Active Directory site.
You have three servers that have Exchange Server 2013 installed named EX1, EX2 and EX3.
All three servers have the Client Access server role and the Mailbox server role installed.
The Active Directory site links and costs are configured as shown in the exhibit. (Click the Exhibit button.)
Site B is designated as a hub site. EX2 fails.
You discover that all email messages sent from the users in Site A to the users in Site C are queued on a server in Site A.
You need to ensure that the email messages are sent to Site C as quickly as possible.
What should you do first?
![107_thumb[1] 107_thumb[1]](http://examgod.com/bdimages/41dd374e231d_E071/107_thumb1_thumb.jpg)
A. Modify the Active Directory site link costs.
B. Configure Site A as a hub site.
C. Modify the Exchange-specific site link cost.
D. Remove the hub site.
Answer: D
QUESTION 108
Your network contains an internal network and a perimeter network.
The internal network contains four offices.
The perimeter network is located in a separate office.
Each internal office has a direct WAN link to all other internal offices.
Each of the four offices that make up the internal network is configured as an Active Directory site. The Active Directory sites and site links are configured as shown in the exhibit. (Click the Exhibit button.)
Your company has an Exchange Server 2013 organization.
Each site contains two servers that have the Mailbox server role and the Client Access server role installed. To the perimeter network, you deploy two servers that have Exchange Server 2010 Service Pack 2 (SP2) and the Edge Transport server role installed.
You configure an Edge Subscription to Site1.
You deploy a new email notification application to Site4.
The application will send 25,000 email messages daily to external recipients.
You need to identify which WAN links will have increased traffic from the new email application. Which WAN link or links should you identify? (Each answer presents part of the solution. Choose all that apply.)
![108_thumb[1] 108_thumb[1]](http://examgod.com/bdimages/41dd374e231d_E071/108_thumb1_thumb.jpg)
A. The WAN link between Site4 and the perimeter network
B. The WAN link between Site4 and Site3
C. The WAN link between Site1 and the perimeter network
D. The WAN link between Site4 and Site1
E. The WAN link between Site4 and Site2
Answer: CE
Explanation:
C: the traffic will increase on the single WAN link on the perimeter network.
E: The traffic will increase between Site4 and Site2 since the cost of this link (5) plus the cost of the link between Site2 and Site1 (1) is lower the cost on the direct link between Site4 and Site1 (10).
Incorrect answers:
Not A: There is no WAN link between Site4 and the perimeter network.
Not B: The cost of the WAN link between site3 and site3 is high (10). This path will not be chosen.
Not D: There is no WAN link between Site4 and Site1.
QUESTION 109
You have network contoso.com. contoso.com consist of AD DS Domain contoso.com.
All Servers running Windows Server 2012 and all Clients running Windows 8 Pro.
Server1 runs Mailbox Server Role and Client Access Server Role.
You are configuring Anti-Spam Filtering on Server1.
You need to ensure that all emails with words "Free Credit Check" are rejected unless the email is sent to Finance Distribution Group.
You also need to ensure that all emails from partner company Domain name adatum.com bypass the Anti-Spam Filter.
You run the Add-ContentFilterPhrase and add the words "Free Credit Check"
What should you do next?
A. Run the Set-TransportConfig and Set-ContentFilterConfig
B. Run the Set-SenderReputationConfig and Set-TransportConfig
C. Run the Set-ContentFilterConfig and Set-RecipientFilterConfig
D. Run the Set-SenderFilterConfig and Set-RecipientFilterConfig
Answer: A
Explanation:
http://technet.microsoft.com/en-gb/library/bb201691(v=exchg.150).aspx
http://www.jaapwesselius.com/2013/01/10/installing-exchange-server-2013-part-iii/
http://zaliasrobotas.blogspot.co.uk/2013/11/how-to-enable-and-configure-spam-filter.html
http://www.techieshelp.com/exchange-2013-enable-anti-spam/
QUESTION 110
You are evaluating the implementation of a Database Availability Group (DAG).
You need to recommend changes to the planned implementation to minimize the loss of large email messages if a single DAG member fails.
What should you recommend changing?
A. The preference of the mail exchanger (MX) records
B. The duration of single item recovery
C. The intervals of shadow redundancy
D. The size of the transport dumpster
Answer: C
Explanation:
Shadow redundancy intervals will need to be ammended
SafetyNet is a component of Shadow Redundancy. -> .
http://technet.microsoft.com/en-us/library/dd351027(v=exchg.150).aspx
Example 1:
ShadowResubmitTimeSpan on Set-TransportConfig
3 hours
How long a server waits before deciding that a primary server has failed and assumes ownership of shadow messages in the shadow queue for the primary server that’s unreachable.
Example 2:
SafetyNetHoldTime on Set-TransportConfig
2 days
How long successfully processed messages are retained in Safety Net. Unacknowledged shadow messages eventually expire from Safety Net after the sum of SafetyNetHoldTime and
MessageExpirationTimeout on Set-TransportService.
Braindump2go New Released Premium 70-341 Exam Dumps Guarantee You a 100% Exam Success Or We Promise Full Money Back! Download Microsoft 70-341 Exam Dumps Full Version From Braindump2go Instantly!
http://www.braindump2go.com/70-341.html
2015 70-341 Dumps VCE Latest Updated By Braindump2go Today (91-100) Free New Updated 70-341 Practice Tests Dumps Questions and Answers from Microsoft Exam Center Braindump2go Guarantere You 100% 70-341 Pass (111-120)
Comments are currently closed.