13 03 2017
[2017-New-Version]Exam 210-250 Dumps PDF 70q Free Offered by Braindump2go[21-30]
2017 March New 210-250 Exam Dumps and Exam Questions Free Shared Here Today!
Free Instant Download 210-250 Exam Dumps (PDF & VCE) 70Q&As from www.Braindump2go.com Today!
100% Real Exam Questions! 100% Exam Pass Guaranteed!
1.|NEW 210-250 Exam Dumps (PDF & VCE) 70Q&As Download:
http://www.braindump2go.com/210-250.html
2.|NEW 210-250 Exam Questions & Answers Download:
https://1drv.ms/f/s!AvI7wzKf6QBjgnzFpAHsSmXP9zrJ
QUESTION 21
In computer security, which information is the term PHI used to describe?
A. private host information
B. protected health information
C. personal health information
D. protected host information
Answer: C
QUESTION 22
Which security monitoring data type requires the most storage space?
A. full packet capture
B. transaction data
C. statistical data
D. session data
Answer: A
QUESTION 23
Which type of exploit normally requires the culprit to have prior access to the target system?
A. local exploit
B. denial of service
C. system vulnerability
D. remote exploit
Answer: A
QUESTION 24
Which identifier is used to describe the application or process that submitted a log message?
A. action
B. selector
C. priority
D. facility
Answer: D
QUESTION 25
Which concern is important when monitoring NTP servers for abnormal levels of traffic?
A. Being the cause of a distributed reflection denial of service attack.
B. Users changing the time settings on their systems.
C. A critical server may not have the correct time synchronized.
D. Watching for rogue devices that have been added to the network.
Answer: C
QUESTION 26
Drag and Drop Question
Drag the technology on the left to the data type the technology provides on the right.
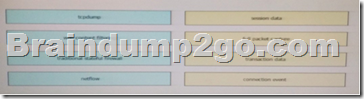
Answer:
![image_thumb[1] image_thumb[1]](http://examgod.com/bdimages/2017-New-Version21-30_9BC0/image_thumb1_thumb.png)
QUESTION 27
Which protocol is primarily supported by the third layer of the Open Systems Interconnection reference model?
A. HTTP/TLS
B. IPv4/IPv6
C. TCP/UDP
D. ATM/ MPLS
Answer: D
QUESTION 28
A firewall requires deep packet inspection to evaluate which layer?
A. application
B. Internet
C. link
D. transport
Answer: A
QUESTION 29
Which two protocols are used for email (Choose two )
A. NTP
B. DNS
C. HTTP
D. IMAP
E. SMTP
Answer: CE
QUESTION 30
Drag and Drop Question
Drag the data source on the left to the left to the correct data type on the right.
![image_thumb[2] image_thumb[2]](http://examgod.com/bdimages/2017-New-Version21-30_9BC0/image_thumb2_thumb.png)
Answer:
![image_thumb[3] image_thumb[3]](http://examgod.com/bdimages/2017-New-Version21-30_9BC0/image_thumb3_thumb.png)
!!!RECOMMEND!!!
1.|NEW 210-250 Exam Dumps (PDF & VCE) 70Q&As Download:
http://www.braindump2go.com/210-250.html
2.|NEW 210-250 Study Guide Video:
https://youtu.be/LMVKGDJtwow
[2017-New-Version]Full Version 210-250 Exam Dumps (VCE and PDF) 70Q for Free Download[11-20] [2017-New-Version]Braindump2go Free 210-250 Questions and Answers Released Today[31-40]
Comments are currently closed.