13 05 2016
[2016-Fortinet-Official]Updated NSE5 Exam Collection & NSE5 New Dumps from Braindump2go[NQ21-NQ30]
2016 May News: Fortinet Network Security Analyst NSE5 Exam Querstions New Released Today in Braindump2go.com Online IT Certification Exams Study Website!
Vendor: Fortinet
Exam Code: NSE5
Exam Name: Fortinet Network Security Analyst
NEW QUESTIONS 21 – NEW QUESTYION 30
QUESTION 21
A firewall policy has been configured for the internal email server to receive email from external parties through SMTP. Exhibits A and B show the antivirus and email filter profiles applied to this policy.
Exhibit A:
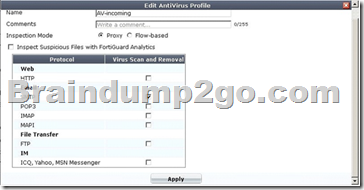
Exhibit B:
![image_thumb[1] image_thumb[1]](http://examgod.com/bdimages/8f4dbe320219_CEDA/image_thumb1_thumb_3.png)
What is the correct behavior when the email attachment is detected as a virus by the FortiGate antivirus engine?
A. The FortiGate unit will remove the infected file and deliver the email with a replacement message to alert the recipient that the original attachment was infected.
B. The FortiGate unit will reject the infected email and the sender will receive a failed delivery message.
C. The FortiGate unit will remove the infected file and add a replacement message. Both sender and recipient are notified that the infected file has been removed.
D. The FortiGate unit will reject the infected email and notify the sender.
Answer: B
QUESTION 22
In order to match an identity-based policy, the FortiGate unit checks the IP information. Once inside the policy, the following logic is followed:
A. First, a check is performed to determine if the user’s login credentials are valid. Next, the user is checked to determine if they belong to any of the groups defined for that policy. Finally, user restrictions are determined and port, time, and UTM profiles are applied.
B. First, user restrictions are determined and port, time, and UTM profiles are applied. Next, a check is performed to determine if the user’s login credentials are valid. Finally, the user is checked to determine if they belong to any of the groups defined for that policy.
C. First, the user is checked to determine if they belong to any of the groups defined for that policy. Next, user restrictions are determined and port, time, and UTM profiles are applied. Finally, a check is performed to determine if the user’s login credentials are valid.
Answer: A
QUESTION 23
An administrator configures a FortiGate unit in Transparent mode on the 192.168.11.0 subnet. Automatic Discovery is enabled to detect any available FortiAnalyzers on the network.
Which of the following FortiAnalyzers will be detected? (Select all that apply.)
A. 192.168.11.100
B. 192.168.11.251
C. 192.168.10.100
D. 192.168.10.251
Answer: AB
QUESTION 24
An end user logs into the full-access SSL VPN portal and selects the Tunnel Mode option by clicking on the “Connect” button. The administrator has enabled split tunneling.
![image_thumb[2] image_thumb[2]](http://examgod.com/bdimages/8f4dbe320219_CEDA/image_thumb2_thumb.png)
Given that the user authenticates against the SSL VPN policy shown in the image below, which statement below identifies the route that is added to the client’s routing table.
A. A route to destination matching the `WIN2K3′ address object.
B. A route to the destination matching the `all’ address object.
C. A default route.
D. No route is added.
Answer: A
QUESTION 25
Which of the following components are contained in all FortiGate units from the FG50 models and up? (Select all that apply.)
A. FortiASIC content processor.
B. Hard Drive.
C. Gigabit network interfaces.
D. Serial console port.
Answer: AD
QUESTION 26
Which of the following pieces of information can be included in the Destination Address field of a firewall policy?
A. An IP address pool, a virtual IP address, an actual IP address, and an IP address group.
B. A virtual IP address, an actual IP address, and an IP address group.
C. An actual IP address and an IP address group.
D. Only an actual IP address.
Answer: B
QUESTION 27
DLP archiving gives the ability to store session transaction data on a FortiAnalyzer unit for which of the following types of network traffic? (Select all that apply.)
A. SNMP
B. IPSec
C. SMTP
D. POP3
E. HTTP
Answer: CDE
QUESTION 28
Which of the following products can be installed on a computer running Windows XP to provide personal firewall protection, antivirus protection, web and mail filtering, spam filtering, and VPN functionality?
A. FortiGate
B. FortiAnalyzer
C. FortiClient
D. FortiManager
E. FortiReporter
Answer: C
QUESTION 29
A FortiGate 100 unit is configured to receive push updates from the FortiGuard Distribution Network, however, updates are not being received. Which of the following statements are possible reasons for this? (Select all that apply.)
A. The external facing interface of the FortiGate unit is configured to use DHCP.
B. The FortiGate unit has not been registered.
C. There is a NAT device between the FortiGate unit and the FortiGuard Distribution Network.
D. The FortiGate unit is in Transparent mode.
Answer: ABC
QUESTION 30
Which of the following statements describes the method of creating a policy to block access to an FTP site?
A. Enable Web Filter URL blocking and add the URL of the FTP site to the URL Block list.
B. Create a firewall policy with destination address set to the IP address of the FTP site, the Service set to FTP, and the Action set to Deny.
C. Create a firewall policy with a protection profile containing the Block FTP option enabled.
D. None of the above.
Answer: B
2016 Valid NSE5 Exam Preparation Materials:
1.| Latest NSE5 PDF Dumps and NSE5 VCE Dumps 240Q&As – 100% Exam Pass Guaranteed: http://www.braindump2go.com/nse5.html
2.| Newest NSE5 Exam Questions PDF – Google Drive: https://drive.google.com/folderview?id=0B75b5xYLjSSNRGszMUtRSkg5VHc&usp=sharing
[2016-Fortinet-Official]Free Braindump2go NSE5 Latest Dumps Download[NQ1-NQ20] [2016-Fortinet-Official]2016 Latest Braindump2go NSE5 Questions Instant Download[NQ31-NQ40]
Comments are currently closed.