23 04 2014
2014 Cisco 100-101 Exam Dump(81-90)
QUESTION 81
What are two recommended ways of protecting network device configuration files from outside network security threats? (Choose two.)
A. Allow unrestricted access to the console or VTY ports.
B. Use a firewall to restrict access from the outside to the network devices.
C. Always use Telnet to access the device command line because its data is automatically
encrypted.
D. Use SSH or another encrypted and authenticated transport to access device configurations.
E. Prevent the loss of passwords by disabling password encryption.
Answer: BD
QUESTION 82
A receiving host has failed to receive all of the segments that it should acknowledge. What can the host do to improve the reliability of this communication session?
A. decrease the window size
B. use a different source port for the session
C. decrease the sequence number
D. obtain a new IP address from the DHCP server
E. start a new session using UDP
Answer: A
QUESTION 83
Which command enables IPv6 forwarding on a cisco router?
A. ipv6 host
B. ipv6 unicast-routing
C. ipv6 local
D. ipv6 neighbor
Answer: B
QUESTION 84
Refer to the exhibit. A host is connected to switch port fa0/3. The host and switch have been fully configured for IP connectivity as shown. However, the indicator LED on switch port fa0/3 is not on, and the host cannot communicate with any other hosts including those connected to VLAN 2 on the same switch. Based on the given information, what is the problem?
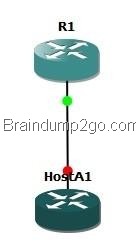
A. switch port fa0/3 is not configured as a trunk port
B. there is a bad cable
C. the switch has been assigned an incorrect subnet mask
D. switch port fa0/3 has been blocked by STP
E. the switch and the host must be in the same subnet
Answer: B
QUESTION 85
Identify the four valid IPv6 addresses. (Choose four.)
A. ::
B. ::192:168:0:1
C. 2000::
D. 2001:3452:4952:2837::
E. 2002:c0a8:101::42
F. 2003:dead:beef:4dad:23:46:bb:101
Answer: ABEF
QUESTION 86
Which two statements describe characteristics of IPv6 unicast addressing? (Choose two.)
A. Global addresses start with 2000::/3.
B. Link-local addresses start with FE00:/12.
C. Link-local addresses start with FF00::/10.
D. There is only one loopback address and it is ::1.
E. If a global address is assigned to an interface, then that is the only allowable address for the interface.
Answer: AD
QUESTION 87
A network administrator is trying to add a new router into an established OSPF network. The networks attached to the new router do not appear in the routing tables of the other OSPF routers. Given the information in the partial configuration shown below, what configuration error is causing this problem?
Router(config)# router ospf 1
Router(config-router)# network 10.0.0.0 255.0.0.0 area 0
A. The process id is configured improperly.
B. The OSPF area is configured improperly.
C. The network wildcard mask is configured improperly.
D. The network number is configured improperly.
E. The AS is configured improperly.
F. The network subnet mask is configured improperly.
Answer: C
Explanation:
When configuring OSPF, the mask used for the network statement is a wildcard mask similar to an access list. In this specific example, the correct syntax would have been “network 10.0.0.0 0.0.0.255 area 0.”
QUESTION 88
Which statement is true?
A. An IPv6 address is 64 b long and is represented as hexadecimal characters.
B. An IPv6 address is 32 b long and is represented as decimal digits.
C. An IPv6 address is 128 b long and is represented as decimal digits.
D. An IPv6 address is 128 b long and is represented as hexadecimal characters.
Answer: D
QUESTION 89
What information does a router running a link-state protocol use to build and maintain its topological database? (Choose two)
A. hello packets
B. SAP messages sent by other routers
C. LSAs from other routers
D. beacons received on point-to-point links
E. routing tables received from other link-state routers
F. TTL packets from designated routers
Answer: AC
QUESTION 90
ROUTER# show ip route
192.168.12.0/24 is variably subnetted, 9 subnets, 3 masks
C 192.168.12.64 /28 is directly connected, Loopback1
C 192.168.12.32 /28 is directly connected, Ethernet0
C 192.168.12.48 /28 is directly connected, Loopback0
O 192.168.12.236 /30 [110/128] via 192.168.12.233, 00:35:36, Serial0
C 192.168.12.232 /30 is directly connected, Serial0
O 192.168.12.245 /30 [110/782] via 192.168.12.233, 00:35:36, Serial0
O 192.168.12.240 /30 [110/128] via 192.168.12.233, 00:35:36, Serial0
O 192.168.12.253 /30 [110/782] via 192.168.12.233, 00:35:37, Serial0
O 192.168.12.249 /30 [110/782] via 192.168.12.233, 00:35:37, Serial0
O 192.168.12.240/30 [110/128] via 192.168.12.233, 00:35:36, Serial 0
To what does the 128 refer to in the router output above?
A. OSPF cost
B. OSPF priority
C. OSPF hop count
D. OSPF ID number
E. OSPF administrative distance
Answer: A
Explanation:
The first parameter is the Administrative Distance of OSPF (110) while the second parameter is the cost of OSPF.
If you want to pass the Cisco 100-101 Exam sucessfully, recommend to read latest Cisco 100-101 Dump full version.
2014 Cisco 100-101 Exam Dump(71-80) 2014 Cisco 100-101 Exam Dump(91-100)

Comments are currently closed.